#networking protocol service
Explore tagged Tumblr posts
Text

5G technology can offer advantages that have the potential to revolutionize the hotel landscape. Let’s take some time to dive deeper into how and why this next-generation wireless technology could have major implications for your business. Read More...
#voip technology#business phones#5G Technology#5G Network#Cloud technology#pbx system#voip advantages#phonesuite direct#voip phone#hotel hospitality#phonesuite dealers#hotel phone system#pbx communications#VoIP Protocol#SIP Protocol#Pms integration#Call Booking#Hotel Technology#Cloud Reservation System#Hotel industry#Business phones#Cloud-based#cloud based#Voip Service#Caller ID
2 notes
·
View notes
Text
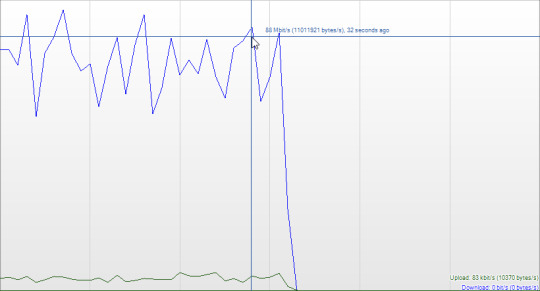
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text

The telephone system is an essential tool for successful hospitality operations, and where evolving communication is key to providing exceptional customer service. A robust phone system ensures that orders are accurately taken, reservations are managed, and customer inquiries are answered. Read More...
#cloud technology#unified communications#VoIP#phonesuite voiceware#hotel pbx#cloud telephony#ip telephony#telephone#hotel hospitality#hotel phone installation#phone#hotel phone system#voiceware by phonesuite#internet protocol#phonesuite#data network#call routing#Softphone#Phone service#Business VoIP#VoIP service#VoIP phone system#VoIP Phone#VoIP System#Hosted VoIP#Desk phone
1 note
·
View note
Text
What is IP SLA (Cisco)? | Definition from TechTarget
What is Cisco IP SLA? Internet protocol service level agreement (IP SLA) is a network performance monitoring (NPM) feature of the Cisco Internetwork Operating System (Cisco IOS) that enables an IT professional to collect information about network performance in real time. Cisco IOS IP SLA provides a way to monitor network performance and report on it with the help of statistics. IP SLA generates…

View On WordPress
1 note
·
View note
Note
You may have posted about this before, but im very curious about you saying "email was a mistake" because it's such a cemented part of online communication. Is it the technology?
Email became infrastructural in a way that it was never intended to be and wasn't designed for.
There is too much momentum toward email being the primary means of business communication that unless there is a massive technology shift we're unlikely to see wide adoption of an alternative and email takes up so much space in the IT space that it's hard to say what the alternative would be.
Much of what used to be email now happens in company chat apps, which I think is an improvement in many ways, but you chat with your coworkers in a way that you're unlikely to chat with a client or send a quote to a prospect.
A huge amount of effort goes into making email better, and making email systems talk to each other, and making email secure because it is so ubiquitous that you can't realistically ask people not to use it.
But it's fucking terrible and we're asking too much of a set of protocols that was supposed to send small, not-very-private, communications between academics.
Why can't you send big files via email? Because that's not what email is for.
Why is it a pain in the ass to send encrypted emails? Because that's not what email is for.
Why aren't your emails portable, and easy to move from one service to another? Because that's not what email is for.
Why are emails so easy to spoof? Because they were never meant to be used the way we use them so there was no reason to safeguard against that fifty years ago
It's like how social security cards were never meant to be used as one of your major super serious government IDs where all of your activity through all of your life is tracked, because if they knew they needed a system for that they probably would have built a better one in the first place.
Nobody who sat down and developed email looked more than half a century into the future and went "so people are going to be using this system to create identities to access banking and medical records and grocery shopping and school records so we'd better make sure that it's robust enough to handle all of that" because instead they were thinking "Neat! I can send a digital message to someone on a different computer network than the one that I am literally in the same building as."
We think of email as, like, a piece of certified mail that is hand delivered in tamperproof packaging to only the intended recipient who signs for it with their thumbprint and a retina scan when it is, instead, basically a postcard.
It would be absurd to try to do the things people do with email with postcards, and it's *nearly* as absurd to try to do them via email.
1K notes
·
View notes
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
So … I rarely talk about politics on here. I prefer to take action in real-life, and put my time and money where my mouth is.
But, as a medical student and a United States citizen, there are some things I need you to know.
- Unfortunately, many states have laws requiring healthcare providers ask patients about their immigration status. You do not have to answer this. Despite what is encoded into law, you will not be turned away nor reported, especially if you are seeking emergency services. Do not let fear stop you from getting the care you need, that’s what the government wants.
- An executive order has withdrawn the United States from the World Health Organization. While the WHO is not perfect, they are responsible for some of the most comprehensive research networks, vaccine initiatives, healthcare surveillance systems, and pandemic response protocols around the globe. Every healthcare provider and medical student I know is worried about what this means for our future and the standard of care we are able to provide nationally.
- Dismantling DEI programs only serves to hurt already marginalized communities. Contrary to what the White House claims, DEI initiatives do not allow “less qualified” applicants to enter the workforce. Instead, they provide individuals who have systematically been given less opportunities a more equitable playing field. For example, only about 6.9% of physicians identify as Hispanic and about 5.7% of physicians identify as Black or African American in the United States. This is extremely disproportionate when looking at ethnicity statistics of the country as a whole. And it largely comes down to the same root cause — lack of resources. No medical school is accepting unqualified applicants, that’s simply a fact. What DEI initiatives do promote, however, is qualified applicants to study and eventually become healthcare providers. Because guess what? Research has shown that physicians of color are most likely to practice in underserved communities and provide medical care to some of the patients who need it most.
There is so much more I want to say that can’t be adequately condensed into a short post on tumblr. But what I can do is try to do my small part in educating how current events are going to trickle down and affect national healthcare as we know it.
My comments, messages, and inbox are always open for anyone who wants to talks.
#united states#us politics#usa politics#usa#us elections#donald trump#trump administration#anti trump#trump
238 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Text

In this blog post, we look at some emerging trends in 4G/5G/6G technology and explore how embracing them can help you develop your business into the hotel of tomorrow. Read More...
#voip technology#pbx system#5G and 6G#VoIP#5G network#6G Network#Cloud VoIP#VoIP Solution#voip provider#voip services#hotel phone system#voip phone#phonesuite dealers#phonesuite direct#voip advantages#hotel hospitality#business voip#voip solutions#SIP Protocol#Cloud-based#cloud based solutions#Cloud#business phones#pbx communications#cloudcomputing#Unified communications
0 notes
Text
Stolen Imperial Files - Captain Howzer

SUBJECT FILE: #7569-HWZ-RYL STATUS: DESERTER – ACTIVE THREAT LEVEL: high DESIGNATION: CT-7569 “HOWZER”

AGE: 26 (BIOLOGICAL) SPECIES: HUMAN EYES: BROWN HEIGHT: 6'1" ALIAS: HOWZER HOMEWORLD: KAMINO
TRAITS: EXHIBITS A CALM, STEADYING PRESENCE—COLLECTED, PRINCIPLED, AND PROTECTIVE BY NATURE. TENDS TO FORM DEEP EMOTIONAL BONDS, PARTICULARLY WITH CIVILIANS AND SUBORDINATES, WHICH OFTEN OVERRIDE PROGRAMMED LOYALTY TO COMMAND. SHOWS STRONG INTERNAL CONFLICT BETWEEN DUTY AND CONSCIENCE, LEADING TO ACTS OF DEFIANCE WHEN IMPERIAL ORDERS CONTRADICT PERSONAL ETHICS. INSPIRES TRUST AND LOYALTY AMONG HIS PEERS THROUGH QUIET STRENGTH, EMOTIONAL INTELLIGENCE, AND UNWAVERING RESOLVE. AFFILIATIONS: GAR
BIOGRAPHY
CT-7569, codenamed “Howzer,” is a clone officer formerly assigned to Imperial garrison command on Ryloth during the initial post-war occupation. Publicly considered a model officer, Howzer’s service record within the Republic Army was unblemished, with commendations for loyalty and command efficacy. Following the rise of the Empire, Howzer remained stationed under the directive of Vice Admiral Rampart to enforce martial stability across Twi’lek territories. Subject’s defection occurred during the Ryloth Uprising (see Rebellion Suppression Dossier #RLS-INC-33). During an attempted extraction of known insurgent Cham Syndulla, Howzer openly disobeyed Imperial orders, directly intervening to prevent execution of civilian and rebel targets. Eyewitness reports confirm subject incited clone troopers under his command to stand down and join the resistance, resulting in a failed detention of key insurgents and a compromised garrison post. CT-7569 was detained under Imperial security protocols and listed for tribunal transport to Imperial Justice Station ODR-3. During transit, subject escaped custody under unknown circumstances (see Prisoner Transfer Breach Report #ODR-EVAC-19A). It is suspected that Howzer’s extraction was coordinated by rogue clone elements or sympathetic internal agents. Subsequent sightings across the galaxy have placed CT-7569 in proximity to known clone deserter networks, including cells operating beyond the Mid Rim. A verified field report submitted by CC-3636 confirms visual identification of Howzer on Teth, in the company of CT-7567
PROFILE NOTES Command Proficiency: Trained under Republic High Command; known for adaptive strategy, effective squad cohesion, and exceptional morale leadership. Psychological Deviation: Subject’s behavior during the Ryloth Uprising indicates possible inhibitor chip degradation or suppression. Moral Alignment Shift: Extensive exposure to civilian populations, particularly on Ryloth, may have influenced a psychological realignment. ISB analysts suggest subject exhibits strong empathic bias toward native resistance movements and fellow clones.

THE HUB Ask to join the Tag List!
#green girl productions#echo recon crew#echo recon#ERC#captain howzer#may the fourth#may the 4th#may 4th#may the force be with you#may the fourth be with you#Star Wars#Howzer#the clone wars#tbb howzer#bad batch howzer#clone trooper howzer#star wars rebels#star wars day#star wars au#howzer x oc#Star Wars fanfic#starwars fanart#Howzer fanfiction#Howzer fan art
61 notes
·
View notes
Text
The Rise of DeFi: Revolutionizing the Financial Landscape

Decentralized Finance (DeFi) has emerged as one of the most transformative sectors within the cryptocurrency industry. By leveraging blockchain technology, DeFi aims to recreate and improve upon traditional financial systems, offering a more inclusive, transparent, and efficient financial ecosystem. This article explores the fundamental aspects of DeFi, its key components, benefits, challenges, and notable projects, including a brief mention of Sexy Meme Coin.
What is DeFi?
DeFi stands for Decentralized Finance, a movement that utilizes blockchain technology to build an open and permissionless financial system. Unlike traditional financial systems that rely on centralized intermediaries like banks and brokerages, DeFi operates on decentralized networks, allowing users to interact directly with financial services. This decentralization is achieved through smart contracts, which are self-executing contracts with the terms of the agreement directly written into code.
Key Components of DeFi
Decentralized Exchanges (DEXs): DEXs allow users to trade cryptocurrencies directly with one another without the need for a central authority. Platforms like Uniswap, SushiSwap, and PancakeSwap have gained popularity for their ability to provide liquidity and facilitate peer-to-peer trading.
Lending and Borrowing Platforms: DeFi lending platforms like Aave, Compound, and MakerDAO enable users to lend their assets to earn interest or borrow assets by providing collateral. These platforms use smart contracts to automate the lending process, ensuring transparency and efficiency.
Stablecoins: Stablecoins are cryptocurrencies pegged to stable assets like fiat currencies to reduce volatility. They are crucial for DeFi as they provide a stable medium of exchange and store of value. Popular stablecoins include Tether (USDT), USD Coin (USDC), and Dai (DAI).
Yield Farming and Liquidity Mining: Yield farming involves providing liquidity to DeFi protocols in exchange for rewards, often in the form of additional tokens. Liquidity mining is a similar concept where users earn rewards for providing liquidity to specific pools. These practices incentivize participation and enhance liquidity within the DeFi ecosystem.
Insurance Protocols: DeFi insurance protocols like Nexus Mutual and Cover Protocol offer coverage against risks such as smart contract failures and hacks. These platforms aim to provide users with security and peace of mind when engaging with DeFi services.
Benefits of DeFi
Financial Inclusion: DeFi opens up access to financial services for individuals who are unbanked or underbanked, particularly in regions with limited access to traditional banking infrastructure. Anyone with an internet connection can participate in DeFi, democratizing access to financial services.
Transparency and Trust: DeFi operates on public blockchains, providing transparency for all transactions. This transparency reduces the need for trust in intermediaries and allows users to verify and audit transactions independently.
Efficiency and Speed: DeFi eliminates the need for intermediaries, reducing costs and increasing the speed of transactions. Smart contracts automate processes that would typically require manual intervention, enhancing efficiency.
Innovation and Flexibility: The open-source nature of DeFi allows developers to innovate and build new financial products and services. This continuous innovation leads to the creation of diverse and flexible financial instruments.
Challenges Facing DeFi
Security Risks: DeFi platforms are susceptible to hacks, bugs, and vulnerabilities in smart contracts. High-profile incidents, such as the DAO hack and the recent exploits on various DeFi platforms, highlight the need for robust security measures.
Regulatory Uncertainty: The regulatory environment for DeFi is still evolving, with governments and regulators grappling with how to address the unique challenges posed by decentralized financial systems. This uncertainty can impact the growth and adoption of DeFi.
Scalability: DeFi platforms often face scalability issues, particularly on congested blockchain networks like Ethereum. High gas fees and slow transaction times can hinder the user experience and limit the scalability of DeFi applications.
Complexity and Usability: DeFi platforms can be complex and challenging for newcomers to navigate. Improving user interfaces and providing educational resources are crucial for broader adoption.
Notable DeFi Projects
Uniswap (UNI): Uniswap is a leading decentralized exchange that allows users to trade ERC-20 tokens directly from their wallets. Its automated market maker (AMM) model has revolutionized the way liquidity is provided and traded in the DeFi space.
Aave (AAVE): Aave is a decentralized lending and borrowing platform that offers unique features such as flash loans and rate switching. It has become one of the largest and most innovative DeFi protocols.
MakerDAO (MKR): MakerDAO is the protocol behind the Dai stablecoin, a decentralized stablecoin pegged to the US dollar. MakerDAO allows users to create Dai by collateralizing their assets, providing stability and liquidity to the DeFi ecosystem.
Compound (COMP): Compound is another leading DeFi lending platform that enables users to earn interest on their cryptocurrencies or borrow assets against collateral. Its governance token, COMP, allows users to participate in protocol governance.
Sexy Meme Coin (SXYM): While primarily known as a meme coin, Sexy Meme Coin has integrated DeFi features, including a decentralized marketplace for buying, selling, and trading memes as NFTs. This unique blend of humor and finance adds a distinct flavor to the DeFi landscape. Learn more about Sexy Meme Coin at Sexy Meme Coin.
The Future of DeFi
The future of DeFi looks promising, with continuous innovation and growing adoption. As blockchain technology advances and scalability solutions are implemented, DeFi has the potential to disrupt traditional financial systems further. Regulatory clarity and improved security measures will be crucial for the sustainable growth of the DeFi ecosystem.
DeFi is likely to continue attracting attention from both retail and institutional investors, driving further development and integration of decentralized financial services. The flexibility and inclusivity offered by DeFi make it a compelling alternative to traditional finance, paving the way for a more open and accessible financial future.
Conclusion
Decentralized Finance (DeFi) represents a significant shift in the financial landscape, leveraging blockchain technology to create a more inclusive, transparent, and efficient financial system. Despite the challenges, the benefits of DeFi and its continuous innovation make it a transformative force in the world of finance. Notable projects like Uniswap, Aave, and MakerDAO, along with unique contributions from meme coins like Sexy Meme Coin, demonstrate the diverse and dynamic nature of the DeFi ecosystem.
For those interested in exploring the playful and innovative side of DeFi, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to learn more and join the community.
254 notes
·
View notes
Text
alt text under cut
Alt National Park Service·
Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
64 notes
·
View notes
Text

"Decorate your phone with Tokyo Mew Mew!"
Nakayoshi 10/2002
Magazine Ad for a Tokyo Mew Mew wallpaper using I-mode (I-Mode, stands for Internet. -mode is a mobile internet service popular in Japan. Unlike Wireless Application Protocols, i-mode encompasses a wider variety of internet standards, including web access, e-mail, and the packet-switched network that delivers the data.)
Which will end services in 2026
Scan by MyuMyuCheerCh on X
35 notes
·
View notes
Text
IoT Device Selection
IoT App Development Company: Everything You Need To Know
Get a balance between quality, cost, and time with superior IoT Services for dealing with your business challenges in the best possible manner. We serve global clients with boastful services on a varied scale, with end-to-end network vs. device integration services with the most innovative solutions. Optimize your IoT strategy with meticulous IoT device selection tailored to your goals.
Benefits of IoT Development
The Internet of Things (IoT) is the technology that allows businesses to integrate their service via secondary devices. With IoT, you can build user-friendly apps compatible with various devices, operating systems, and screen resolutions. You can also integrate your smart apps with third-party apps using secure APIs and collect vital user data and behavior on the mobile application to personalize the experience even further.
How to choose a reliable partner for IoT Development?
While analyzing an IoT vendor partner, you should prioritize secure organizations that behold strong web security and development. You must also adopt Full-stack organizations and companies that can establish an ‘all-in-one’ solution that manages a single project’s hardware, mobile interface, and web interface. Opting for a vendor offering these development capabilities and improvements is a much safer bet.
Why TechAhead for IoT App Development?
With over 13+ years of experience delivering cutting-edge digital transformation and mobility solutions, TechAhead has been a major digital partner for globally established companies like Disney, Audi, and American Express. Clutch has ranked us among the top IT IoT development services companies and the top multicultural companies with a strong-willed presence across Los Angeles and Noida.
Who is the top IoT development company?
TechAhead, of course! We have been accelerating business agility and stimulating digital transformation since 2009. Our company was recognized last year as the top IT service provider by Leaders Matrix, an industry-recognized, unbiased ranking entity.
We disrupt the traditional outsourcing model of other IoT companies. We ensure long-term and sustainable success for our customers and the mobile and digital ecosystem. Our relationships with our customers go beyond transactional. Our software development services give entrepreneurial ideas life. We infuse existing mobile and digital platforms with innovation and creativity.
What are the top IoT Apps developed by TechAhead?
We are a world-class digital transformation and mobility solution company and have delivered over 2,000+ project developments on Android, iOS, and cross-platform compatible apps for global brands. We recently announced the launch of “The Healthy Mummy” fitness app, which was recently ranked the world’s #1 Mum’s fitness app, attracting over 2M+ users and adding to many of our success stories.
What about Data security and integrity of IoT Apps?
All TechaAhead development practices are highly efficient and secure thanks to meticulous adherence to security practices and data governance at every step. Our development process considers the devices connected, cloud computing requirements, IoT platforms, and security while developing IoT mobile applications. We ensure that our IoT apps follow all the guidelines and protocols for the highest security.
How to get IoT app maintenance help and post-launch support?
Our role remains strong after the go-live. TechAhead takes full responsibility for the smooth functioning of IoT solutions in your company. With platform support services, maintenance, and the support of process management, our team will monitor your app’s success, it’s adaptability and remove any bugs/errors as per our client’s business needs and user reviews.
In conclusion, the world of IoT app development is a realm of boundless possibilities. Through TechAhead's expertise and commitment, businesses can harness the power of IoT to create user-friendly apps, ensure data security, and drive innovation. TechAhead's track record of success, recognition, and dedication to post-launch support make it a reliable partner in the journey of IoT app development. With a focus on disruptive innovation and holistic relationships, TechAhead is poised to continue shaping the landscape of IoT solutions, delivering transformative results for businesses worldwide!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text

Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!
42 notes
·
View notes
Note
any pointers for writing fade? neon is my current fixation & i wanna write abt her bc i wanna get back into writing. fadeshock is rlly cute but idk fade all too well 🤍
lobe ur works sm
Oh, this is a fabulous question, I'm going to have a fantastic time answering this, thank you!
First, I want to make clear though that this is just my opinion and my take on Fade's character. You're welcome to write her how you like and if you disagree with my headcanons, that's okay! You're welcome to form your own.
Now, for my answer.
I think when writing Fade it's important to keep in mind that her driving force is loyalty. Almost everything she does is in service to someone she cares about - usually him - and she will pursue this service even to her own detriment.
She blackmailed the Protocol even though they would probably have killed her if she failed, and when they offered to help her and gave her information on how to further her search, she joined them. She throws herself so hard into her work it makes her seriously unwell at times, such as when she got so distressed and sleep-deprived that Brimstone needed to send her on a wellness vacation to Vietnam to recover.
Through her voicelines and additional lore (such as the audio recording of Cypher interrogating her) we can glean that her manner of speaking is informal and "masc". She calls people "abi" in the same way one might say "dude" or "bro". She's friendly with her teammates, offering them coffee and encouragement (and we also know she has a network of friends in the Protocol, with Clove's D&D club for example). She's arrogant and clearly recognises her own skills, but on top of that, we also know that she's heavily depressive, angry, and fearful. She's terrified of losing him, but we know she's beginning to believe he might be dead from when they didn't find him in the Hourglass cells. "You live until you're forgotten, right?"
When I'm writing her I tend to write from the perspective of a woman who's deeply afraid, but not for herself. She sees very little value in her own life, at least when she isn't using her life to serve. She's self-sacrificing and too easily puts herself in harms way if she believes it will protect those she loves, and when she's struggling she isolates herself. From the Vietnam situation, we've seen it takes other people reaching out for her to get the help she needs when things are dire, and when she didn't find him in Hourglass, she was very clearly upset but didn't ask for help, instead kind of solidifying in her resolve to continue the search without giving up on him.
When things are good, I think she's a pretty loving person. A lot of people depict her as edgy all the time but I think that's doing her a disservice, personally. She's depressed and self-sacrificing and I think without help she could very easily fall into dangerous patterns (I imagine she uses smoking, drinking, hookups with strangers etc to cope with how bad she feels).
That said though, she's a good person. She's warm with her teammates and has a sense of humour with them. She can be optimistic in dire situations, too, although likely this is just to avoid accepting the reality of him possibly being dead. I think when she loves someone, she does it in a way that needs communication to work, because she could otherwise love them in a way that could be smothering or overly possessive, but when she doesn't need to be permanently afraid, she'd be a great person to be in love with.
I imagine that love as a concept is very hard for her, now. This is a hc, but I imagine that after the pain of losing him and how close it's come to killing her a number of times now, she'd be terrified of loving people again. I think she'd push people away long before ever accepting she wants them, and it would take a lot of time for her to believe she deserves to love another, especially if she's falling in love before saving him. Loving someone is distraction, it's attention spent off of the trail of hunting him, but it's also shockingly vulnerable. It's putting her heart on the chopping block and hoping her partner won't cut it.
ugh, I love her. Apologies for this really long answer - I really, really love both Fade and Neon and I have a LOT to say about them both, and how they work together. I really enjoyed answering this, thank you so much for the question and I hope this can help a little!
27 notes
·
View notes